We recently moved from dialup to a nice fiber optic connection to the Internet (No, I’m not getting into why it wasn’t until 2008 that we got broadband). Now that we have a good connection with good up and down speeds I decided to turn on port forwarding on our primary router, an AirPort Base Station (802.11n model).
I have all incoming packets forwarded to my Mac OS X Server and things work very well. I can access my server from anywhere. And with a DynDNS account, I can easily remember the address. I’ve been running like this for a little over a month now and I’m starting to get tired of all of those messages in my secure.log and the failed authentications in my SMTP server log.
I seriously don’t understand the desire to hack other people’s systems.
But there are clearly people out there that want to do Bad Things with my server and I need to protect it. Up until now I have been trusting the server services to protect themselves, the OS to protect itself and user accounts to have sufficiently secure passwords.
Trust is a funny thing. It has no place on today’s Internet. Time to lock things down.
- Lock down unnecessary services
- I’d already done this, but I wanted to make sure to mention it. If a service isn’t needed I turned it off. I can always turn it on later. I guess I should mention that Mac OS X Server’s default state is for services to be off.
- Lock down services
- Mac OS X Server includes service access control lists (SACLs). You can allow access to server services based on user or group. Since I want SSH enabled, but I don’t want anyone but me to be able to access the server via SSH I set up my SACL appropriately:
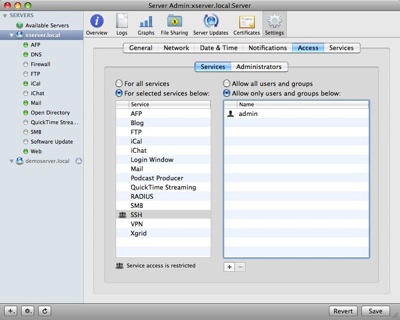
- Configure firewall
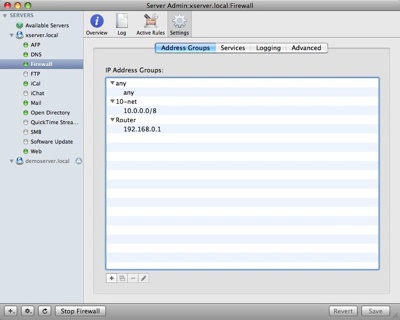
- Mac OS X Server also includes a very customizable firewall. I want to configure it to allow anyone within my home network to access any services but to restrict access to the server to inbound clients. Since all inbound clients will appear to connect to my server from my router’s IP address, I will set up a new Address Group for 192.168.0.1 and restrict to to only the services/ports that I want. The nice thing about this is that I can always change these settings remotely later if I want.
Add the router to an Address Group:
Skip over to Advanced and configure a Deny All rule for the Router. This will set up a default secure state:
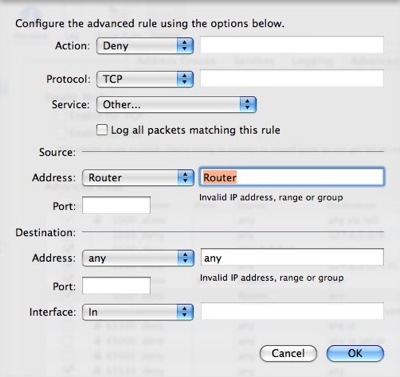
These rules are numbered and processed in order from lower to higher number. The first rule to ‘hit’ will trigger. In our example we will add new rules to allow access to IP ports from the router for particular services. First we’ll allow access to the web server over the standard web port (80):
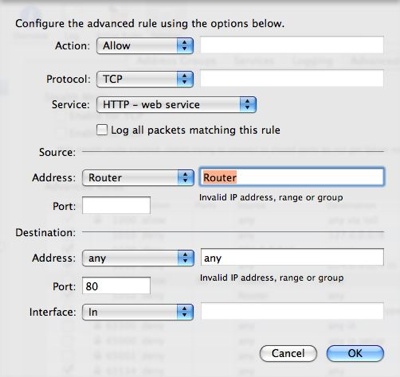
After you add the allow rule make sure it is above the deny rule in the Advanced Rules list by dragging as necessary.
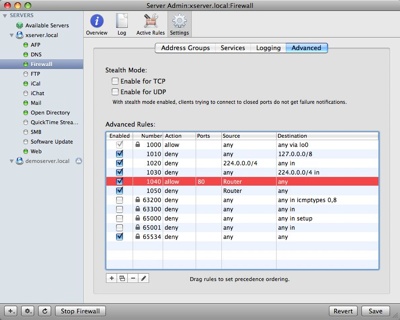
I’ll go ahead and allow access for all of the ports that I want externally accessible.
Now I don’t have to just trust in the services to protect themselves, the OS to protect itself and users to have good passwords. I can trust the firewall to prevent anyone from getting to some services and externally visible services to protect themselves and I guess I’ll still have to trust users to have good passwords. Of course with that, I can use Open Directory password policies…
Next step I’ll enable VPN so that I can get to my home network remotely.
Happy serving!
Technorati Tags: Mac OS X, Mac OS X Server, Security
